30 New Ways For Picking A Cybersecurity Company in UAE
30 New Ways For Picking A Cybersecurity Company in UAE
Blog Article
Top 10 Tips To Assess The Certifications And Compliant Of A Cybersecurity Services Company Located In Dubai, Uae
1. Verify the authenticity of certificationsBegin by verifying that the certifications issued by the company are valid. Verify that the certificates are valid and current by contacting the issuing authority or certification body. Key certifications to consider include ISO 27001, PCI DSS, and copyright, among others. Certificates that are valid prove compliance with security standards.
2. Local Regulatory Compliance
Be familiar with the regulations and laws which govern security in the UAE. For instance, the UAE Data Protection Law or the Dubai Cybersecurity Strategy. Check that the business is compliant with these legal frameworks because non-compliance could lead to legal repercussions and reputational damage.
3. Assess Industry-Specific Standards
Depending on the industry that you are in, certain standards are more crucial. For example, financial institutions and healthcare organizations should be focusing on PCI DSS. Assessing industry-specific certifications ensures that the business has the necessary expertise to handle sector-specific risks.
4. Request Documentation
Demand a full and detailed documentation that demonstrates compliance to relevant standards. This includes audit reports, security policies as well risk management frameworks. These documents will provide you with more insight into how committed the company is to cybersecurity and compliance.
5. For more information, ask about Third-Party Audits.
Find out if the business has regular audits conducted by an external third party. Independent audits offer a more independent evaluation of the compliance and security practices of a firm. Find audit reports from reputable companies that verify the security policies of the business.
6. Evaluate Continuous Improvement Initiatives
Security has advanced and businesses need to show that they're committed to improving. If policies and technologies are updated frequently to keep up with new threats or regulatory changes, this is a good sign. This may mean changing their security policies and continuing training.
7. Review employee training programs
Training employees is essential for the security of your company. Inquire if the company has any programs for training related to compliance and cybersecurity. Regularly scheduled training sessions are crucial to keep employees informed of the most recent threats, and regulations for compliance.
8. Review Incident Response Plans
Know the company's incident response procedures. A well-constructed incident response plan will detail the company's notification process, remediation strategies as well as other elements. Make sure that their protocols comply with the guidelines for compliance and the best practices.
9. Read testimonials from our customers and refer to references
References from clients can verify the company’s compliance and certifications. Testimonials can provide an insights into the effectiveness and reliability in tackling cybersecurity risk, allowing you to assess their credibility within the industry.
10. Research Industry Recognition
Check out the reputation of the company in the cybersecurity community. Find awards, certificates or memberships with professional associations that highlight the company's commitment to compliance and excellence in cybersecurity. The credibility of a company and its expertise are usually closely linked to its reputation. Read the recommended Cybersecurity Company in Dubai for website info including cyber security security, information and cyber security, managed it services security, cyber security company, cyber security software, network and security solutions, it security jobs, cyber security software, cyber security ot, information security usa and more.
Top 10 Tips To Assess The Capabilities To Respond To Incidents Of A Cybersecurity Service Company
1. Understand Incident Response FrameworkBegin by looking at the incident response framework that the company uses. A clearly defined structure, like the NIST Cybersecurity Framework of the SANS Incident Response Process shows that the business follows the best practices in the industry for handling incidents efficiently. Make sure they have a clear and well-organized procedure for dealing with incidents.
2. Evaluate Incident Response Team Expertise
Assess the qualifications, experience, and expertise of every member. Examine certifications such Certified Incident Handlers, or Certified Information Security Professionals. To efficiently manage and minimize incidents, you need an educated team.
Check out the case studies of past incidents
Case studies or other examples of incidents handled by the company are available upon request. Examining their responses to actual scenarios will give insight into the company's effectiveness in speed, efficiency and overall approach to management. Find out in detail how they identified, contained or resolved issues.
4. Verify the availability of 24/7 Incident Response Availability
Check if a company provides 24/7 incident response. A cybersecurity incident can occur any time. A staff that is on call 24/7 can minimize the damage and also speed up recovery.
5. Find out more about incident detection tools
Review the tools and techniques the company utilizes to detect and prevent incidents. The most effective detection tools, like Security Information and Event Management Systems (SIEM) and intrusion detection systems (IDS) can assist detect potential threats faster.
6. Examine Communication Protocols
Find out what protocols for communication are employed by the company in an emergency. Clear and effective communication is crucial for coordinating responses to inform stakeholders, as well as making sure everyone is aware of their roles during an incident. How can they keep their clients up-to-date throughout the entire response?
7. Review Post Incident Review Processes
Inquire about the process of reviewing post-incidents for your business. It is essential to conduct thorough reviews after an incident to discover any lessons that could be gained. Look for companies that implement adjustments based on the reviews to improve their future response efforts.
8. Review the effectiveness of recovery strategies and methods for remediation.
Understand the strategies the company employs to help recover and improve following an incident. Effective recovery plans will outline the process of restoring the systems and data and also addressing any vulnerabilities to prevent recurrences. Find out their plan for building up systems and strengthening them following an incident.
9. Review compliance with regulatory Requirements
Make sure that your incident response capability is affixed to the required legal requirements. Based on the industry you work in, there may be specific requirements regarding reporting incidents and response. The regulations are well-known to companies that can ensure compliance.
10. Get references and testimonials.
Finally, gather references from customers who have used the services of the company's emergency response. Client testimonials provide insight into a company's effectiveness, reliability, overall satisfaction, and the level of service provided to incidents. Check out the most popular penetration testing company in uae for website examples including security by design, cyber security consulting company, best cybersecurity firms, network and security solutions, cyber security requirement, network security software, cybersecurity and technology, it security technologies, inform security, cyber security information and more.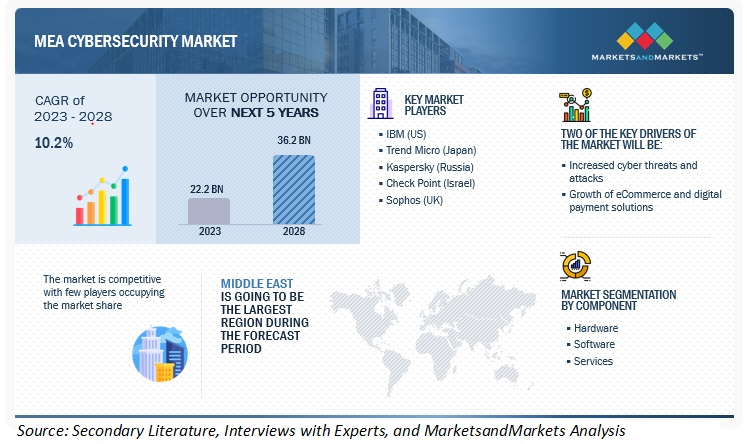
Top 10 Tips To Assess The Security Awareness Training Of A Cybersecurity Service Firm
1. Examine Training ContentStart's evaluation by looking over the contents of the security awareness programs. Be sure the material covers the most important topics such as social engineering and phishing. Additionally, ensure that data security and compliance are included. It is crucial to offer employees an extensive curriculum to help them recognize and respond to threats.
2. Options for customization are offered
A custom-designed training program can satisfy the particular needs of your organization and its culture. Making your training specific to the specific challenges and situations that confront the employees of your organization can improve relevance and engagement.
3. Examine Training Delivery Methods
Learn about the different methods of delivery for training. You can choose from interactive simulations, webinars and online courses and workshops. Different formats can be utilized to meet the needs of various learning styles, and improve overall effectiveness.
4. Interactive Elements
Examine if there are interactive elements in the course like quizzes or simulations. Interactive training improves the learning process and engagement making it easier to apply knowledge in real-world situations.
5. Examine the frequency of updates
Find out the frequency of the training sessions and the frequency at which the material is updated. In light of the ever-changing nature of cybersecurity threats regular training sessions as well as frequent updates to the training curriculum are essential for keeping employees informed about the latest threats and best methods.
6. Measurement effectiveness
Find out how the company evaluates the effectiveness of training. You will find indicators such as pre- and post-training evaluations, participants' feedback and trends in the reporting of incidents. It is essential to analyze the effectiveness of a training program to determine its effectiveness and identify areas for improvement.
7. Check Certification and Compliance
Check if the course will be accompanied by certification at the end. Certifications can enhance employee credibility and show that they've learned the relevant skills. Make sure you align the training to any pertinent requirements for compliance with regulations your company has.
8. Search for testimonials and references.
Gather feedback from organizations that have previously utilized the training services. Testimonials can be a fantastic way to gain insight into how effective the training was and how the participants reacted. Positive feedback can be an indication of the company's credibility in providing effective awareness training.
9. Evaluate Post-Training Support
Ask about the assistance provided after the course is complete. Continuous resources, like refresher courses, newsletters, or access to a knowledge database, can aid in enhancing the learning and keep cybersecurity awareness in the forefront of employees' minds.
10. Evaluation of Engagement and the Building of Culture
Lastly, assess the extent to which the program has helped in creating a culture for security within your business. Look for initiatives that promote continuous awareness. These could include security newsletters and workshops. Security-focused cultures inspire employees to take responsibility for protecting their organization. Follow the recommended iconnect for more info including ai in cybersecurity, cyber security what is, info security, cyber security in usa, secure the data, network security, cyber security education, it security logo, cybersec consulting, inform security and more.